When changes in a repository make a Dependabot pull request out-of-date, Dependabot will automatically rebase it so that it is able to be merged without your manual effort. With this release, if a PR has not been merged for 30 days, Dependabot will stop rebasing it and will include a note about this in the PR body. You will still be able to manually rebase and merge the pull request. We've heard your feedback about Dependabot noisiness and are making Dependabot quieter and more focused on repositories you care about. For enterprise customers, this improvement has the added benefit of enhanced efficiency with your self-hosted GitHub Actions runners. For Enterprise Server customers, this update will be available to you in GHES 3.10.
You can now filter by repository topic or team on the enterprise-level Dependabot, code scanning, and secret scanning pages in security overview.

These improvements have shipped to GitHub.com and will be available in GitHub Enterprise Server 3.9.
Learn more security overview and send us your feedback
Learn more about GitHub Advanced Security
You can now fetch release notes, changelogs and commit history for Docker update pull requests with Dependabot. This will allow you to quickly evaluate the stability risk of the dependency upgrade. To enable support, add the org.opencontainers.image.source label to the Dockerfile with the URL of the source repository. Additionally, the repository should be tagged with the same tags as the published Docker images. This allows Dependabot to understand which repo and commit is associated each version/tag of a Docker image. Here's an example repository demonstrating this setup.
Did you know? Dependabot's internal library for identifying dependency updates is open source. If you notice a Dependabot pull request is missing metadata, you can leverage the transparency of open source to debug the root cause – for example, if the package maintainer needs to fix their metadata annotation.
GitHub Advanced Security customers using secret scanning can now view any secrets exposed historically in an issue's title, description, or comments within the UI or the REST API. This expanded coverage will also detect and surface secrets matching any custom pattern defined at the repository, organization, or enterprise levels.
Following our recent release of generating a software bill of materials from the repository's dependency graph, you can now generate an SBOM for a repository using a new REST API for SBOMs. The resulting JSON will represent the head of the repository's main branch.
Code scanning default setup is now available for Go!
Default setup automatically finds and sets up the best CodeQL configuration for your repository. It detects the languages in the repository and enables CodeQL analysis for every pull request and every push to the default branch and any protected branches. A repository is eligible for default setup if it uses GitHub Actions and contains JavaScript/TypeScript, Python, Ruby or Go.
You can use default setup on your repository's "Settings" tab under "Code security and analysis".

This new feature is available on GitHub.com today, and will also ship with GHES 3.10. More language support will be provided soon, and all other CodeQL-supported languages continue to work using a GitHub Actions workflow file. The options to set up code scanning using API uploads or third party analysis tools remain supported and are unchanged.
For more information on code scanning default setup, see Configuring code scanning automatically.
Users with access to secret scanning alerts can now view metadata for any active GitHub token leaked in their repositories. Metadata includes details like the token's owner, expiration date, and access permissions. With this information, security teams can assess a leak's potential impact and prioritize remedial action accordingly.
This feature builds on our previous release in January, which introduced validity checks for leaked GitHub tokens.
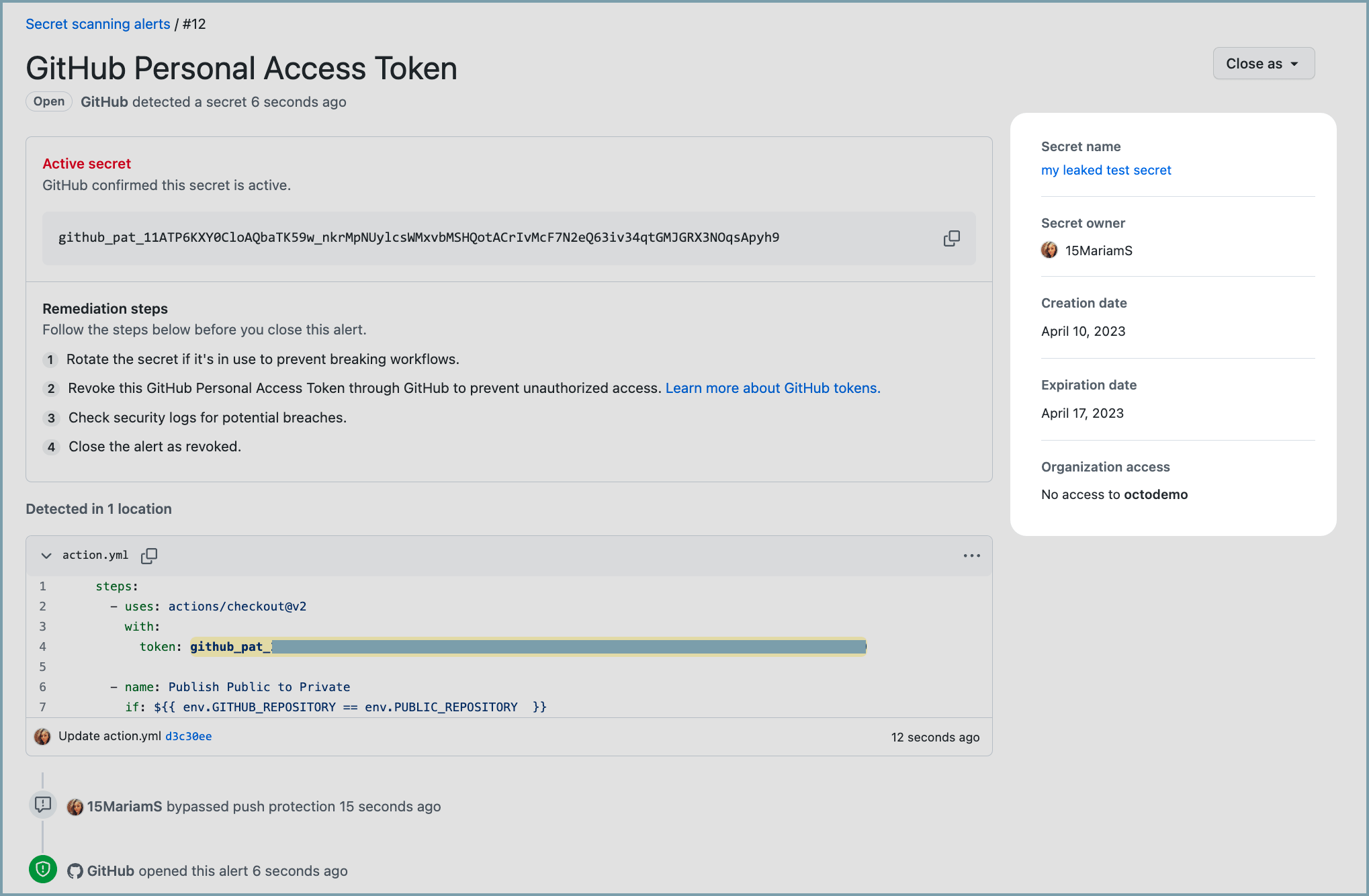
- Learn how to review GitHub token metadata
- Learn more about secret scanning
- Got feedback? Open a discussion in our code security discussion.
GitHub Code Scanning now supports scanning projects built with C#11 / .NET 7 and leveraging the latest language features.
These features include:
- Generic attributes
- Generic math support
- Numeric IntPtr and UIntPtr
- Newlines in string interpolations
- List patterns
- Improved method group conversion to delegate
- Raw string liters
- Auto-default struct
- Pattern match Span or ReadOnlySpan on a constant string
- Extended nameof scope
- UTF-8 string literals
- Required members
- ref fields and ref scoped variables
- File scoped types
C# 11 / .NET 7 support is available by default in GitHub.com code scanning, the CodeQL CLI, and the CodeQL extension for VS Code.
You can now filter by repository topic or team on the organization-level Dependabot, code scanning, and secret scanning pages in security overview.

These improvements have shipped to GitHub.com and will be available in GitHub Enterprise Server 3.9.
GitHub Advanced Security users can now view alert metrics for custom patterns at the repository, organization, and enterprise levels directly from the custom pattern's page. Custom patterns with push protection enabled also show metrics like total secrets blocked and bypassed.
We welcome feedback in our code security discussion.

You can now programmatically view and act on repository advisories via a new REST API. New endpoints to create, view, list, and update advisories are available to all. Additionally, new webhooks have been introduced that will alert maintainers when advisories are published or when a private vulnerability report is submitted.
Current advisory permissions extend to API usage.
The dependency graph shows a summary of the manifest and lock files stored in a repository. The repository view has an updated user experience that includes:
- Search by package name from a paginated list of all dependencies
- Dependency licenses
- Dependabot alerts for dependencies, sorted by severity, and linking to the Dependabot alerts and the Dependabot updates pull request where applicable (only visible for users with priveleges to view the repository's Dependabot alerts)

Access a repository's dependency graph from Insights > Dependency graph.
A software bill of materials (SBOM) is a standardized inventory of a software project's dependencies and associated metadata (versions, licenses, etc). You can now export your repository's dependency graph as an SBOM adhering to the SPDX 2.3 specification.
Click "Export SBOM" on a repository's dependency graph to generate an SBOM representing the head of the main branch. The resulting JSON file will download in your browser. Exporting an SBOM is free for all cloud repositories on GitHub, and can be performed by anyone with read access to a repository.
A supporting REST API to generate SBOMs for repositories will be available in the coming weeks.

The new code scanning tool status page allows users to view the status of CodeQL and other code scanning tools.
The page shows all the tools that are enabled on the repository and provides information about their setup types, configurations, and any relevant failures or warnings. If a tool is not working as expected, this is a good place to start troubleshooting the issue.
You can visit the new tool status page by using the button at the top of the repository's Code Scanning page.

Statuses for the tool
The page indicates three possible statuses for the tool: all configurations are working, some need attention, and some are not working.
Code scanning needs to have received at least one analysis for the default branch to provide a tool status. Only the status of the default branch is reported.
The page shows the latest state of all analysis configurations for the tool. For instance, if you created two separate workflows to scan two distinct parts of the repository independently, the page displays the most recent state of the tool by combining the statuses of both.
The page structure
For each tool, the page provides actionable information about misconfigurations and errors, the number of scanned files per language, the setup types and configurations, the list of rules the tool checks against, and detailed CSV reports.

Error messages
To help you with debugging, the tool status page shows error messages gathered from multiple code scanning system components during tool setup and analysis execution. These include errors from CodeQL, code scanning workflows, SARIF upload limits, and the internal code scanning system.
Third party code scanning tools are not yet able to deliver tool related errors to the page. In the future, these tools will be able to submit error messages to code scanning via SARIF uploads.
Scanned files
A Scanned Files section shows the number of analysed files per language compared to the number of files in the repository.
The section helps you determine whether code scanning tools are operating correctly on your repository and only shows information about languages supported and analysed by the tool while ignoring languages that are present in the repository but are not supported or being analysed by the tool.
This section is not yet displayed for third party code scanning tools. In the future, third party tools will be able to submit error messages to code scanning via SARIF uploads.
Delivery dates
This has shipped to GitHub.com and will be available in GitHub Enterprise Server 3.9.
Learn more about code scanning and the tool status page.
Learn more about GitHub Advanced Security.
We've recently released a few improvements to the slide-out enablement panel on the security coverage page in security overview:
- Active committers for the repository are now visible, providing insight into the number of Advanced Security licenses being utilized. For repositories where Advanced Security is not enabled, the number indicates the number of licenses required to enable the feature.
- Unsaved changes are now clearly labeled with a "Modified" tag. Additionally, the "Save security settings" button now displays the total number of enablement changes being made.
- While a security feature is being enabled, the coverage page will show a status of "Updating…" to keep you informed of the ongoing process.

These improvements have shipped to GitHub.com and will be available in GitHub Enterprise Server 3.9.
Learn more security overview and send us your feedback
Learn more about GitHub Advanced Security

