Level up monitoring and reporting for your enterprise
A high-quality audit log is an essential tool for enterprises to ensure compliance, maintain security, investigate issues, and promote accountability.
GitHub runs on trust
GitHub is the software development platform trusted by millions of developers. With this trust comes a responsibility to constantly improve our security, audit, and compliance solutions with the developer in mind. A high-quality audit log is an essential tool for enterprises to ensure compliance, maintain security, investigate issues, and promote accountability. GitHub has been working hard to add new features to help enterprises gain more visibility into their organizations’ software development and collaboration activities, and operate with greater peace of mind when it comes to security and compliance.
Increase visibility into your enterprise’s activity to achieve new levels of security, compliance and peace of mind
Audit log streaming in the past year
In January 2022, GitHub announced that audit log streaming was generally available. Since then, more than 800 enterprises have configured audit log streaming to one of our six supported streaming endpoints. Audit log streaming enables enterprises to automatically send a stream of near real time data to a storage or Security Information and Event Management (SIEM) system of their choosing.
Audit log streaming enables enterprise owners to empower teams with the the benefits of:
- Data Exploration. Examine streamed events using your preferred tool for querying large quantities of data. The stream contains both audit events and Git events across the entire enterprise account.
- Build near real time threat detection: by analyzing the audit log data in real time, security teams can detect potential threats as they occur and respond quickly to mitigate them. This can help to prevent or limit the impact of a security breach.
- Automate compliance monitoring: audit log streaming enables continuous monitoring of the system to ensure compliance with regulatory requirements. This can help to identify potential compliance issues before they become a problem.
- Discover operational insights: by analyzing the audit log data in near real time, organizations can gain valuable insights into how their systems are being used. This can help to optimize performance, identify areas for improvement, and inform decision-making.
- Data Continuity. You can pause the stream for up to seven days without losing any audit data.
- Data retention. Keep your exported audit logs and Git events data as long as you need to.
But audit logs will only be as good as the data they contain. So, we’ve also been hard at work leveling up both event coverage and context.
API requests are available via audit log streaming
We recently announced a public beta where GitHub Enterprise Cloud customers can add REST API requests targeting private and internal repositories to their audit log stream. The team will soon expand this functionality to cover additional API endpoints, including GraphQL.
Many GitHub users leverage GitHub’s APIs to extend and customize their GitHub experience. However, use of APIs can create unique security and operational challenges for enterprises.
With the introduction of targeted API requests in audit log streaming, enterprise owners are now able to:
- Better understand and analyze API usage targeting their private and internal repositories.
- Identify and diagnose potentially misconfigured applications or integrations.
- Identify the authentication tokens being used by specific applications or integrations.
- Troubleshoot API contributing to API rate limiting.
- Leverage API activity when performing forensic investigations; and
- Develop API specific anomaly detection algorithms to identify potentially malicious API activity.
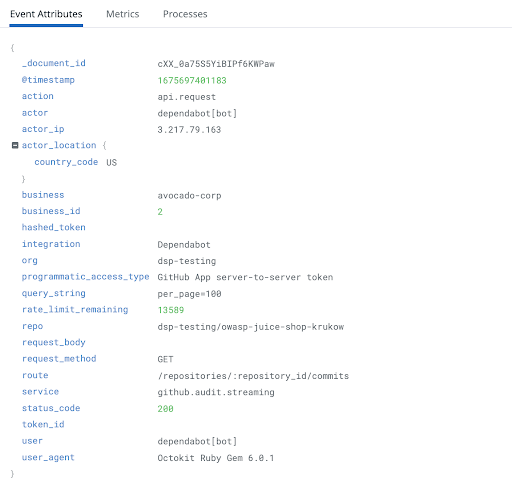
To add API requests to your audit log, follow these instructions for enabling audit log streaming of API requests.
Searching your audit log for token activity
Stolen and compromised credentials are the number one cause of data breaches across the industry. According to the IBM Security’s 2022 Cost of a Data Breach Report, “In 2022, the most common initial attack vectors were compromised credentials at 19% of [data] breaches.” To help enterprise and organization owners better understand token activity, the audit log has added additional authentication token metadata to audit log events. Admins can now query their audit logs for activity associated with a specific authentication token. They will be better equipped to detect and trace activity associated with corrupt authentication tokens. This feature becomes increasingly valuable when paired with the ability to stream API requests, as it provides a new level of observability into API usage within your enterprise, including the method of authentication being used successfully or unsuccessfully. In doing so, customers can better equip their enterprises to detect and contain potentially malicious API activity.
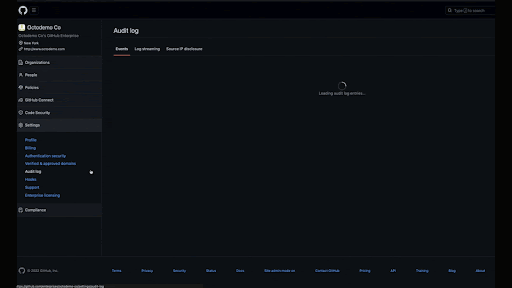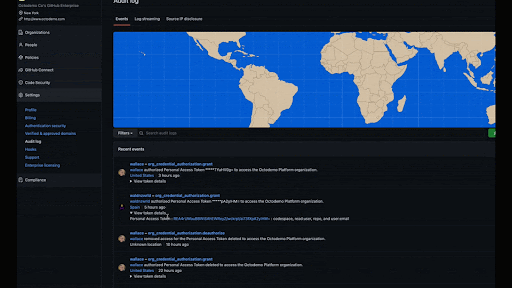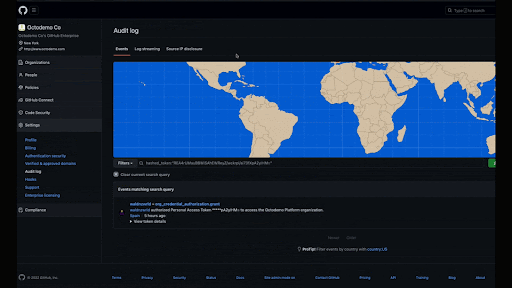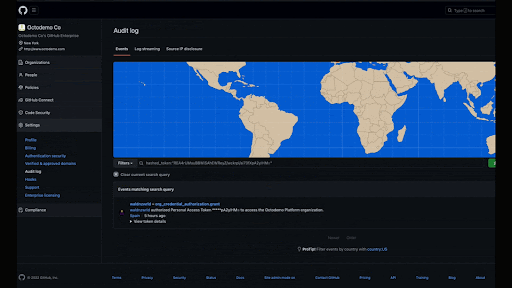
To learn more, read our documentation on identifying audit log events performed by an access token.
External Identity data within the audit log
GitHub Enterprise customers need to link their organization members’ activity back to the individual’s corporate identity. If you centrally manage your users’ identities and applications with an identity provider (IdP), you can configure Security Assertion Markup Language (SAML) single sign-on (SSO) to protect your organization’s resources on GitHub. With System for Cross-domain Identity Management (SCIM), administrators can also automate the exchange of user identity information between systems. If your organization uses SAML SSO, you can implement SCIM to add, manage, and remove organization members’ access to GitHub Enterprise Cloud.
GitHub Enterprise Cloud customers can now participate in a private beta displaying external identity data as part of audit log events. Customers enrolled in the beta can expect to see external identity data when performing actions within an enterprise or organization with SAML SSO or SCIM enabled via the GitHub user interface or accessing enterprise assets via GitHub’s APIs. Soon, support for displaying external identity data for git events will also be added.
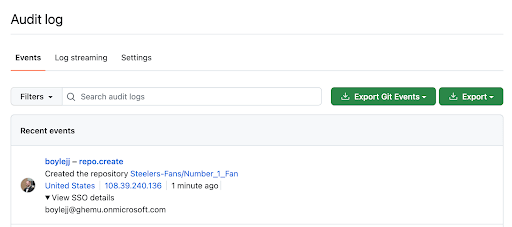
With the addition of this new metadata to the audit log, organization and enterprise owners can easily link audit log activity with the user’s corporate identity providing increased visibility into the identity of the user and streamlining correlation of logs from multiple systems to quickly and easily.
Enterprise owners interested in participating in the private beta should reach out to your GitHub account manager or contact our sales team to have this feature enabled for your enterprise. Once enabled, enterprise and organization owners can provide feedback at the logging SAML SSO authentication data for enterprise and org audit log events community discussion page.
SIEM integrations
GitHub Advanced Security (GHAS) is a developer-first application security platform. GitHub provides the Security Overview page for a high-level view of the security status of their organization or to identify problematic repositories that require intervention. However, security operations professionals may want to run more powerful queries, create customized dashboards and visualizations, or desire to join GitHub alerts with additional data from environment logs. To meet these needs we’re excited to announce our integrations with security information and event management (SIEM) providers, Splunk, Microsoft Sentinel, DataDog, Elastic, Sumo Logic, and Panther. With these integrations, GHAS data can be easily exported to external reporting SIEM tools, enabling users to improve their security posture by increasing visibility into application security events.
By integrating GHAS with a SIEM solution, you can stitch together findings identified within the GitHub platform with other data, such as a Configuration Management Database (CMDB), user directory, or asset attribution system. This allows you to see events from your GHAS environment within the risk-based context of your business data. Some examples include:
- Severe vulnerabilities in your high-profile or user-facing applications
- A count of security alerts for each business unit
- Secrets resolved on a per-team basis
- The average time to remediate a vulnerability
- Which repositories depend on a vulnerable dependency
You can also join GitHub Advanced Security data with GitHub Audit Log data, so, for example, you could see if an API token identified by secret scanning was used after it was leaked. These integrations give you a great starting point to build interesting insights.
Wrap up
A high-quality audit log is an essential tool for enterprises to ensure compliance, maintain security, investigate issues, and promote accountability. GitHub has been working hard to create an audit log that provides a comprehensive dataset rich in context that enterprises use with their preferred security stack. GitHub recommends enabling the new audit log features to secure access to all data available to your enterprise, and consider extending the utility of our audit data by streaming your audit log to a supported streaming endpoint and making use of one of our SIEM integrations.
Tags:
Written by
Related posts

How to streamline GitHub API calls in Azure Pipelines
Build a custom Azure DevOps extension that eliminates the complexity of JWT generation and token management, enabling powerful automation and enhanced security controls.

When to choose GitHub-Hosted runners or self-hosted runners with GitHub Actions
Comparing GitHub-hosted vs self-hosted runners for your CI/CD workflows? This deep dive explores important factors to consider when making this critical infrastructure decision for your development team.

Enhance build security and reach SLSA Level 3 with GitHub Artifact Attestations
Learn how GitHub Artifact Attestations can enhance your build security and help your organization achieve SLSA Level 3. This post breaks down the basics of SLSA, explains the importance of artifact attestations, and provides a step-by-step guide to securing your build process.