Accelerate security adoption in your organization
The GitHub Services Engineers have released the Advanced Security Enforcer GitHub Action to enable organizations to utilize code scanning in a consistent and automated way.

Adopting GitHub Advanced Security features like code scanning and secret scanning can greatly improve an organization’s security posture. It actually detects and prevents security issues in code by allowing you to see security issues in your pull requests as part of your code review process. Today, the path to rolling those features out to your organization just got a lot easier!
The Advanced Security Enforcer GitHub Action was built by the GitHub Services Engineers to enable a large government agency to utilize code scanning in a consistent and automated way. As the agency continues to grow, they can rest assured that each new repository will be configured for code scanning. This enables them to find high-priority, exploitable security issues in their code at the scale of their entire organization. Now, it has been open sourced so everyone can use and improve it!
What is the Advanced Security Enforcer?
The Advanced Security Enforcer is a GitHub Action available on the GitHub Marketplace. Organizations that want newly created code repositories using a compatible language can run the action nightly. This means teams don’t have to start from a template repository and they will still be brought into compliance. The following languages are compatible with code scanning at this time with more coming soon!
- C/C++
- Java
- C#
- Python
- Go
- JavaScript
- TypeScript
How it works
When you’ve configured a repository in your organization to start running this action, any time you create a new repository, a pull request will be opened in that repository with a configuration file for code scanning. You just need to supply the action with access to your organization so that it can determine when new repositories are created.
To get started, create a new repository in the organization you want to use this action in and copy the default workflow file from the GitHub Actions page. Here is what it looks like when I do that in my demo organization.
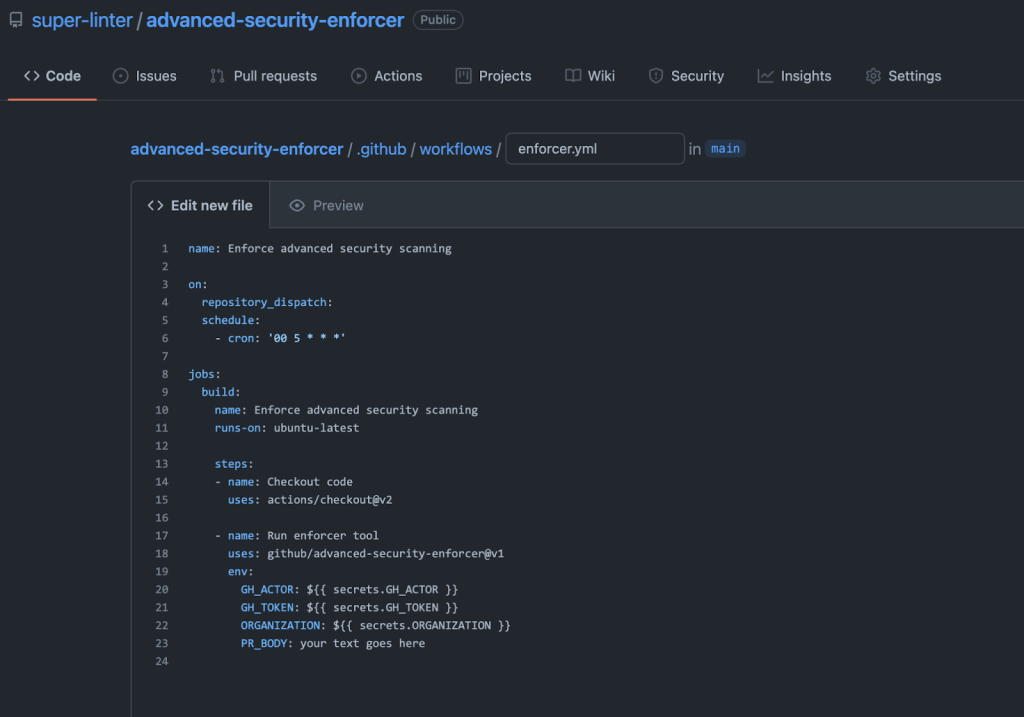
Then you will need to set up the repository secrets GH_ACTOR, GH_TOKEN, and ORGANIZATION. GH_ACTOR should just represent a valid email address for your organization. This allows the action to get a higher rate limit when interfacing with the GitHub API. GH_TOKEN should be a token with repo read permissions to all repositories in the organization—preferably from a service account. Lastly, the ORGANIZATION should just be the name of the organization as it appears in GitHub.
Now that you have set that up, you can see the previous action runs as they are available daily.
Join in the fun
We encourage you to set up this action and start the process of improving your organization’s security today.
How can I contribute?
We’re always looking to improve this action, and are eager to hear how it is working for you. If you’d like to help contribute to this action, check out our contributing guide.
Learn more about the Advanced Security Enforcer
Tags:
Written by
Related posts

How to streamline GitHub API calls in Azure Pipelines
Build a custom Azure DevOps extension that eliminates the complexity of JWT generation and token management, enabling powerful automation and enhanced security controls.

When to choose GitHub-Hosted runners or self-hosted runners with GitHub Actions
Comparing GitHub-hosted vs self-hosted runners for your CI/CD workflows? This deep dive explores important factors to consider when making this critical infrastructure decision for your development team.

Enhance build security and reach SLSA Level 3 with GitHub Artifact Attestations
Learn how GitHub Artifact Attestations can enhance your build security and help your organization achieve SLSA Level 3. This post breaks down the basics of SLSA, explains the importance of artifact attestations, and provides a step-by-step guide to securing your build process.