What’s new in security and user management for GitHub Enterprise
Learn how you can securely manage users with the latest ships for GitHub Enterprise.
Over the past few weeks, we have released several new features to help our GitHub Enterprise customers secure and manage users at an enterprise level. Learn how you can securely manage users with GitHub Enterprise’s latest ships!
Here’s what’s new!
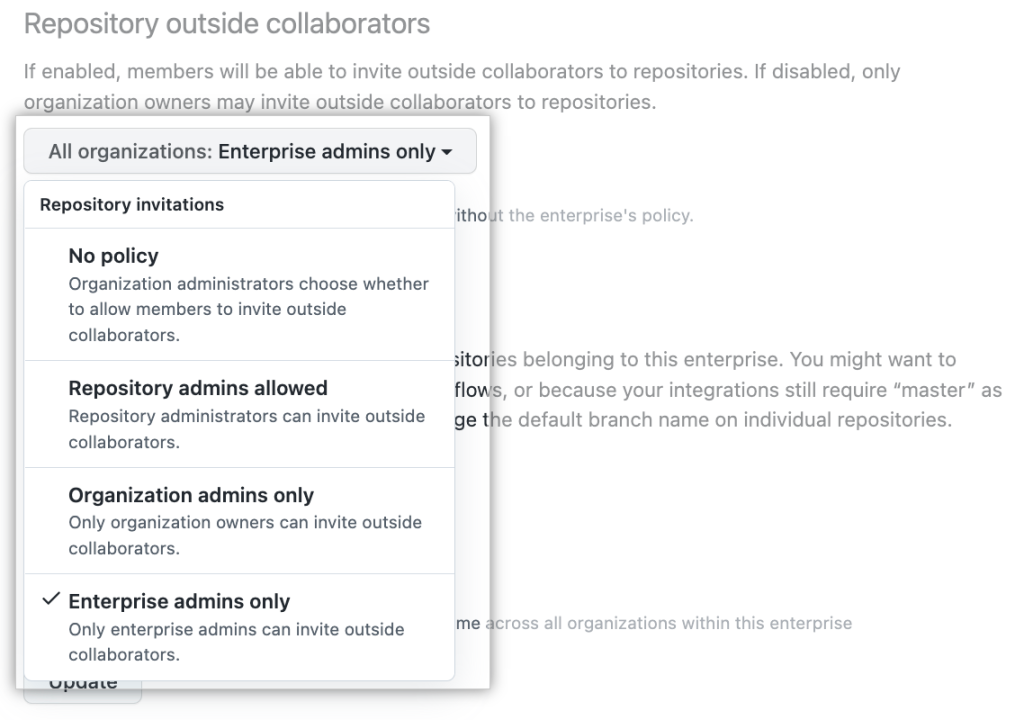
Limit who can invite outside collaborators to enterprise administrators
Enterprise owners can now prevent organization owners from inviting outside collaborators to repositories in their enterprise. In the “Repository outside collaborators” policy dropdown, we’ve included an additional option labeled “Enterprise admins only.” This option limits the ability to invite outside collaborators strictly to enterprise administrators.
Read our GitHub Changelog and documentation to learn more about repository management policies.
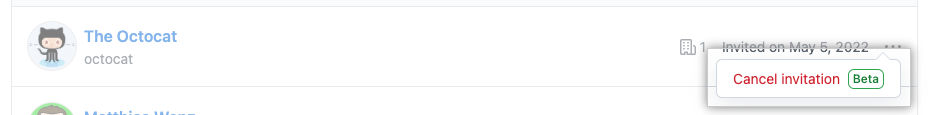
Revoke pending member invitations
Another new feature now available in public beta is that enterprise owners have the ability to revoke pending member invitations. To view pending members and revoke a pending invitation, navigate to the “Pending invitations” page within your enterprise account.
Learn more about this feature via our Changelog and documentation.
View actor IP addresses in your GitHub Enterprise Cloud audit log
Now in public beta, GitHub Enterprise account owners can view actor IP addresses in the audit log for events associated with their private repositories. In this case, an actor is defined as a user that initiates an event within GitHub Enterprise. Disclosing actor IP addresses within audit logs is a long-awaited feature for our Enterprise customers, because it enables them to meet their security and compliance needs. IP addresses are only shared if an Enterprise member takes action against their GitHub Enterprise-owned asset, such as a private repository, project board, issue, or GitHub Action within the enterprise organization. We do not report when someone pushes code to a public repository or a GitHub Enterprise member pushes code to private repositories that are not part of their enterprise’s organization.
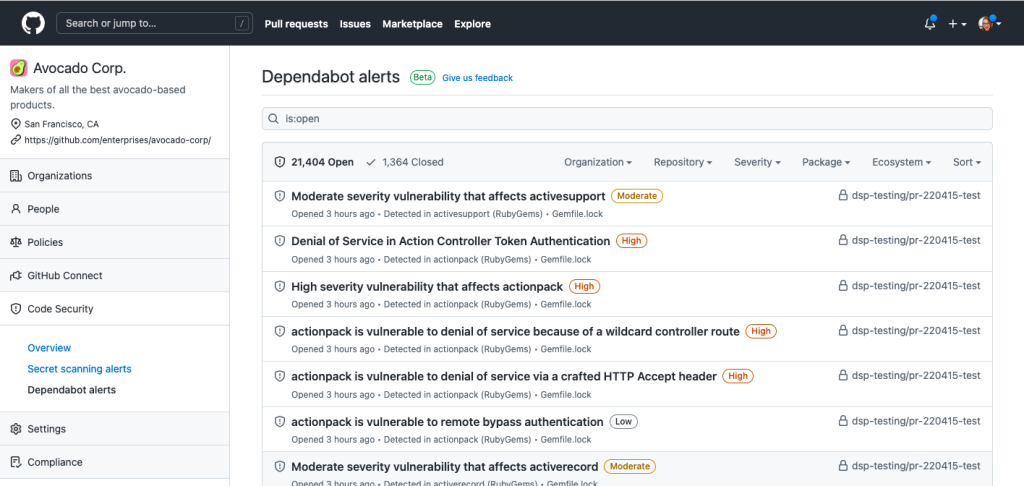
View Dependabot alerts across the enterprise
GitHub Advanced Security customers can now view Dependabot alerts at the enterprise level. This new UI capability in public beta displays a repository-centric view of application security risks, an alert-centric view of all secret scanning, and Dependabot alerts. We plan to include alert-centric views for code scanning in the near future!
Read our Changelog and documentation to learn more about security overview.
Conduct dry runs for custom secret scanning pattern
GitHub Advanced Security customers can also conduct dry runs for custom secret scanning patterns. Conducting dry runs allows admins to understand a pattern’s impact across the entire enterprise and hone in on the pattern before publishing and generating alerts.
Check out our Changelog and our documentation for more information
To learn more about how to keep your organization secure, check out our docs on managing and reviewing security settings.
Tags:
Written by
Related posts

How to streamline GitHub API calls in Azure Pipelines
Build a custom Azure DevOps extension that eliminates the complexity of JWT generation and token management, enabling powerful automation and enhanced security controls.

When to choose GitHub-Hosted runners or self-hosted runners with GitHub Actions
Comparing GitHub-hosted vs self-hosted runners for your CI/CD workflows? This deep dive explores important factors to consider when making this critical infrastructure decision for your development team.

Enhance build security and reach SLSA Level 3 with GitHub Artifact Attestations
Learn how GitHub Artifact Attestations can enhance your build security and help your organization achieve SLSA Level 3. This post breaks down the basics of SLSA, explains the importance of artifact attestations, and provides a step-by-step guide to securing your build process.