Introducing GitHub Sudo Mode
In the ongoing effort to keep our users safe, we recently took inspiration from the Unix sudo command. We wanted to require password confirmation for dangerous actions on GitHub.com, but…
In the ongoing effort to keep our users safe, we recently took inspiration from the Unix sudo command. We wanted to require password confirmation for dangerous actions on GitHub.com, but we didn’t want to force you to be constantly entering your password.
Meet GitHub’s “sudo mode”
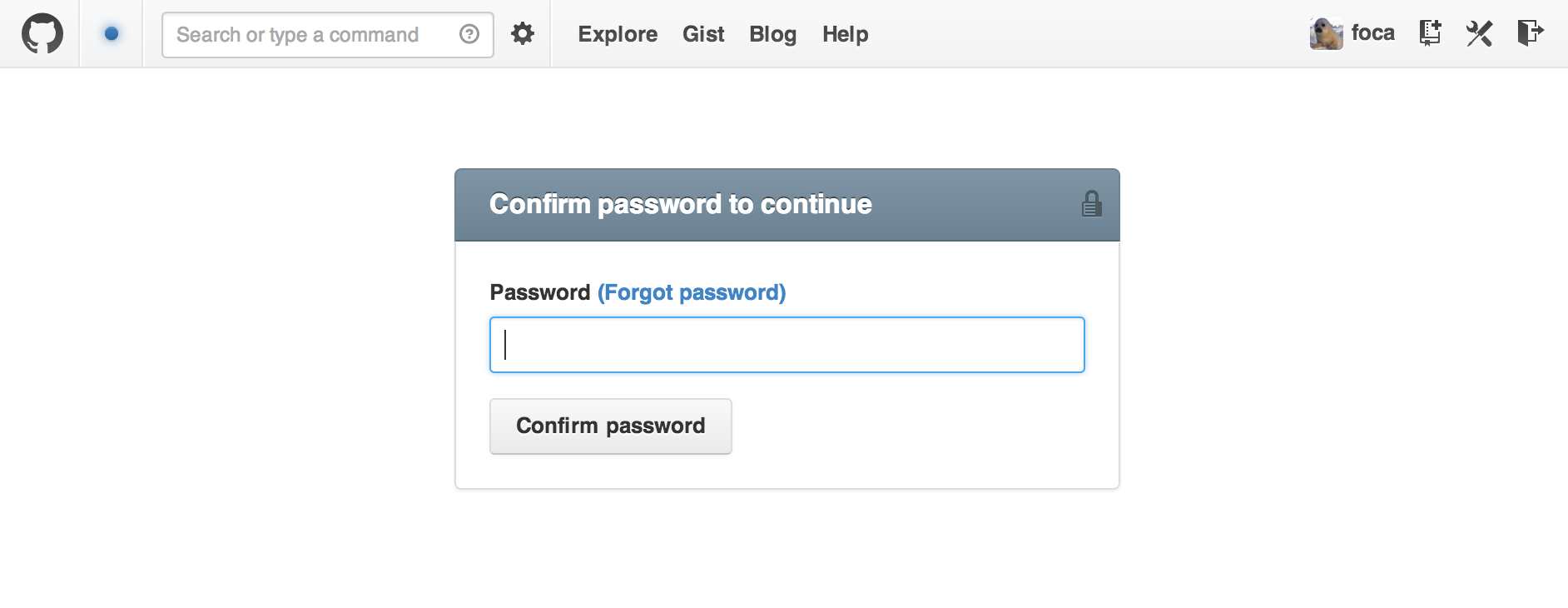
Dangerous actions (e.g. adding email addresses or public keys) will now require password confirmation. If you’re deep in the zone and you’re doing a lot of these dangerous actions, we’ll only ask you to re-authenticate every few hours.
With this balance of security and convenience, we help you keep your account safe, without getting in your way. Feedback is always welcome. Enjoy!
Written by
Related posts

We need a European Sovereign Tech Fund
Open source software is critical infrastructure, but it’s underfunded. With a new feasibility study, GitHub’s developer policy team is building a coalition of policymakers and industry to close the maintenance funding gap.

GitHub Availability Report: June 2025
In June, we experienced three incidents that resulted in degraded performance across GitHub services.

From pair to peer programmer: Our vision for agentic workflows in GitHub Copilot
AI agents in GitHub Copilot don’t just assist developers but actively solve problems through multi-step reasoning and execution. Here’s what that means.