GitHub now publishes malware advisories in the GitHub Advisory Database
To combat the prevalence of malware in the open source ecosystem, GitHub now publishes malware occurrences in the GitHub Advisory Database. These advisories power Dependabot alerts and remain forever free and usable by the community.
Mistakes are the most common cause of vulnerabilities in open source software, but they are not the only cause. Bad actors also attempt to introduce malicious software, known as malware, into open source. Details about malware can be hard to keep track of because malware is typically taken down and is not eligible for the usual disclosure process where vulnerabilities are assigned a CVE and placed in the National Vulnerability Database (NVD).
GitHub discovers malware through multiple means such as automated scanning, security research, and community discovery. Starting today, after a malicious package is removed, we will also create an advisory to document the malware in the GitHub Advisory Database.
Dependabot alerts for malware advisories
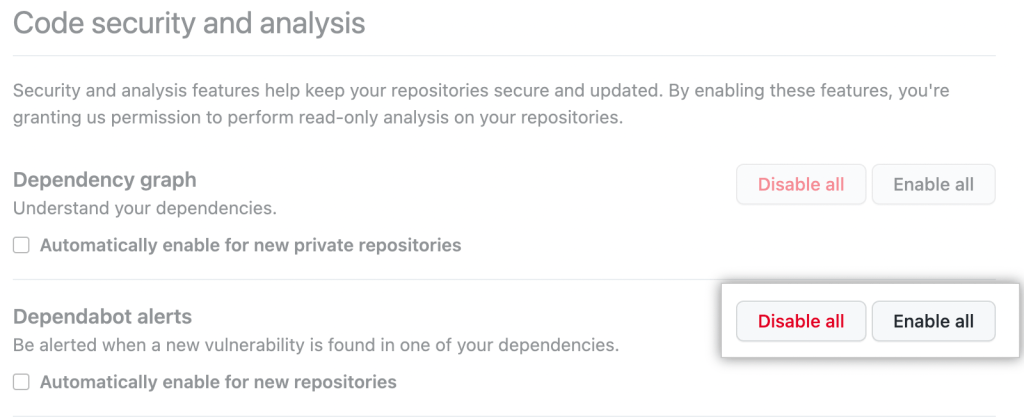
Malware advisories already power Dependabot alerts for impacted GitHub users. If you already use Dependabot, you’re covered with no additional action. To receive alerts on malware advisories and vulnerabilities, you can enable Dependabot by selecting enable all under the “Code security and analysis” tab.
Learn more about GitHub supply chain security solutions
The GitHub Advisory Database publishes security advisories that power GitHub’s supply chain security capabilities, including Dependabot alerts and Dependabot security updates. The data is licensed under a Creative Commons license and has been since the database’s inception, making it forever free and usable by the community. For more information about our supply chain security capabilities, check out the following pages:
- Learn about managing vulnerable dependencies on GitHub
- Visit the GitHub Advisory Database
Tags:
Written by
Related posts

How to catch GitHub Actions workflow injections before attackers do
Strengthen your repositories against actions workflow injections — one of the most common vulnerabilities.

Modeling CORS frameworks with CodeQL to find security vulnerabilities
Discover how to increase the coverage of your CodeQL CORS security by modeling developer headers and frameworks.

CVE-2025-53367: An exploitable out-of-bounds write in DjVuLibre
DjVuLibre has a vulnerability that could enable an attacker to gain code execution on a Linux Desktop system when the user tries to open a crafted document.