How to secure your end-to-end supply chain on GitHub
Securing your projects is no easy task, but end-to-end supply chain security is more top of mind than ever. We’ve seen bad actors expand their focus to taking over user…
Resources for securing your supply chain, building more secure applications, and staying up-to-date with the latest vulnerability research. Get comprehensive insights into the latest security trends—and news from the GitHub Security Lab. You can also check out our documentation on code security on GitHub to find out how to keep your code and applications safe.

Securing your projects is no easy task, but end-to-end supply chain security is more top of mind than ever. We’ve seen bad actors expand their focus to taking over user…
If there’s one habit that can make software more secure, it’s probably input validation. Here’s how to apply OWASP Proactive Control C5 (Validate All Inputs) to your code.

Anyone can now provide additional information to further the community’s understanding and awareness of security advisories.
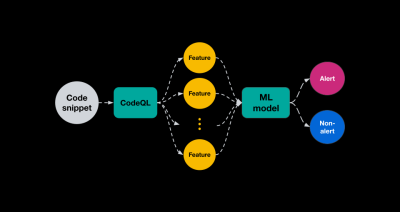
A behind-the-scenes peek into the machine learning framework powering new code scanning security alerts.
Practical tips on how to apply OWASP Top 10 Proactive Control C4.
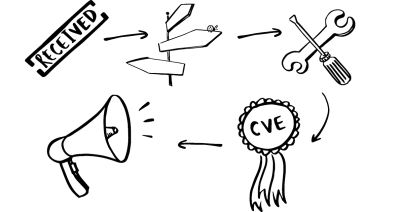
A comprehensive guide for vulnerability reporters.
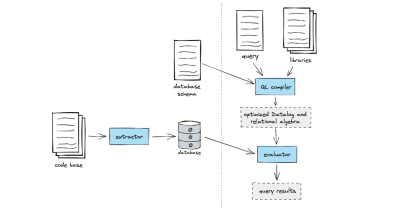
A deep dive into how GitHub adds support for new languages to CodeQL.

Starting today, we are rolling out mandatory 2FA to all maintainers of top-100 npm packages by dependents.
When it comes to secure database access, there’s more to consider than SQL injections. OWASP Top 10 Proactive Control C3 offers guidance.

The GitHub Security Lab’s CodeQL bounty program fuels GitHub Advanced Security with queries written by the open source community.

In this post, I’ll discuss how to apply OWASP Proactive Control C2: Leverage security frameworks and libraries.

Use GitHub’s security features to assess Apache Log4j exposure and, where possible, mitigate this vulnerability within your GitHub repositories.
How to exploit a double-free vulnerability in Ubuntu’s accountsservice (CVE-2021-3939)
GitHub has partnered with the OpenSSF and Project Sigstore to add container image signing to our default “Publish Docker Container” workflow.

GitHub Actions now supports OpenID Connect for secure deployment to different cloud providers via short-lived, auto-rotated tokens.
Build what’s next on GitHub, the place for anyone from anywhere to build anything.