Secure your GitHub account with GitHub Mobile 2FA
GitHub continues to improve account security and developer experience with a new 2FA mechanism in GitHub Mobile on iOS and Android.
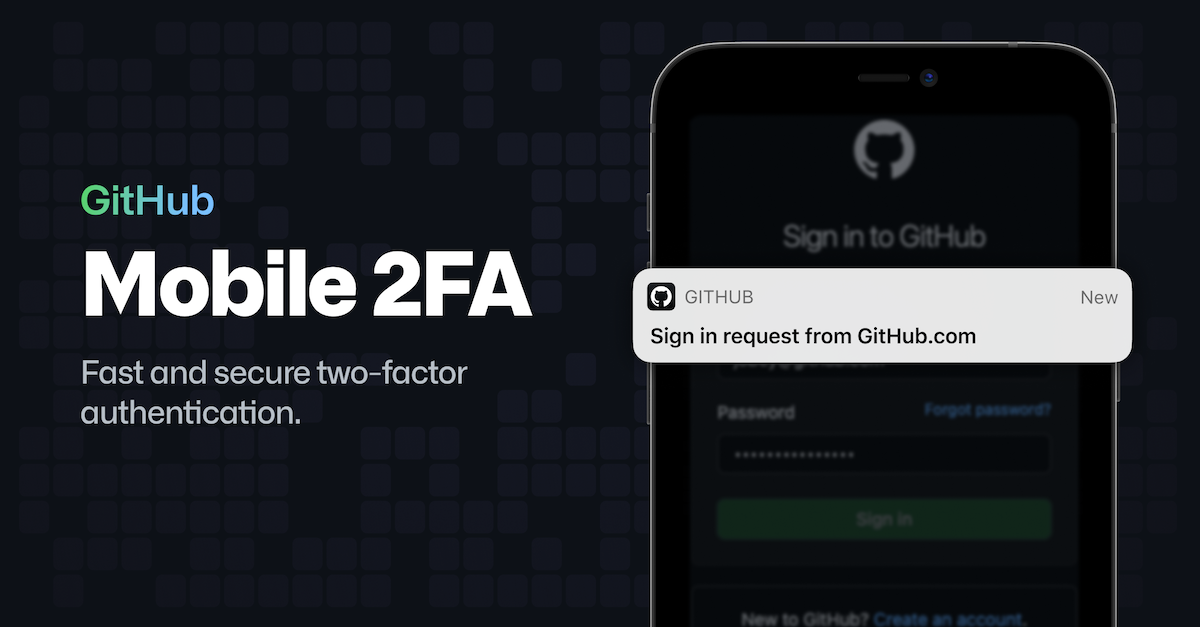
GitHub is committed to keeping our platform secure and enabling developers to secure their accounts. One way we’re doing that is by helping more developers adopt two-factor authentication (2FA) for their accounts. Over the past year, we’ve led the way in improving developer account security with the introduction of support for security keys as an authentication mechanism for git operations and enforcing two factor authentication for all npm publishers.
Today, we are announcing that you can use GitHub Mobile on iOS and Android as an easy-to-use two factor authentication mechanism. This option sits alongside our existing channels: security keys and WebAuthn, one-time passcodes, and SMS. GitHub Mobile provides a strong alternative to existing one-time passcode options offered by third-party applications and via SMS, with an experience that is fully baked into the GitHub services you already use.
GitHub Mobile 2FA will be available to all GitHub users in the App Store and Play Store this week.
Get Started
If you have 2FA configured on your GitHub account and the mobile app installed, update to the latest version of GitHub Mobile in the App Store or Play Store to start using Mobile 2FA immediately.
If you’re not already using the mobile app, you can install it now and sign in to your account. And if you haven’t set up 2FA, set it up via your account security settings. You’ll need to set up 2FA with SMS or another time-based one-time password (TOTP) app first to start using Mobile 2FA.
Once set up, you’ll receive a push notification to your mobile device when you sign in to your GitHub.com account on any browser. You can approve or reject the sign in- attempt. If you approve it, you’ll be logged into GitHub.com immediately.

If you already set up 2FA with a security key, GitHub will use that as the primary two factor authentication channel. Security keys provide the strongest available protection of your account credentials. Read more about how GitHub is integrating authentication with security keys.
GitHub continues to invest in account security to help secure the broader supply chain. We are hard at work on making additional investments in this space for both npm and GitHub, including additional capabilities for GitHub Mobile as an authentication mechanism and increasing adoption for 2FA, so stay tuned!
Read more about securing your account with two factor authentication.
Tags:
Written by
Related posts

We need a European Sovereign Tech Fund
Open source software is critical infrastructure, but it’s underfunded. With a new feasibility study, GitHub’s developer policy team is building a coalition of policymakers and industry to close the maintenance funding gap.

GitHub Availability Report: June 2025
In June, we experienced three incidents that resulted in degraded performance across GitHub services.

From pair to peer programmer: Our vision for agentic workflows in GitHub Copilot
AI agents in GitHub Copilot don’t just assist developers but actively solve problems through multi-step reasoning and execution. Here’s what that means.