Learn more about Dependabot alerts, security updates, and version updates.
A smarter, quieter Dependabot
Dependabot is getting a little smarter—and, a little quieter—by reducing bot-based noise from repositories based on your interaction with Dependabot.
In 2022, Dependabot automatically generated more than 75 million pull requests, which developers used to keep their dependencies up-to-date and to address millions of specific vulnerabilities. Moving forward, Dependabot is getting a little smarter—and, a little quieter—by reducing bot-based noise from repositories based on your interaction with Dependabot.
We’ve been listening to your feedback and making Dependabot more focused on the repositories you care about. In addition to a recent ship to ensure Dependabot version updates are off-by-default for forks, as of today, Dependabot will now automatically cease creating pull requests on inactive repositories.
What’s changing?
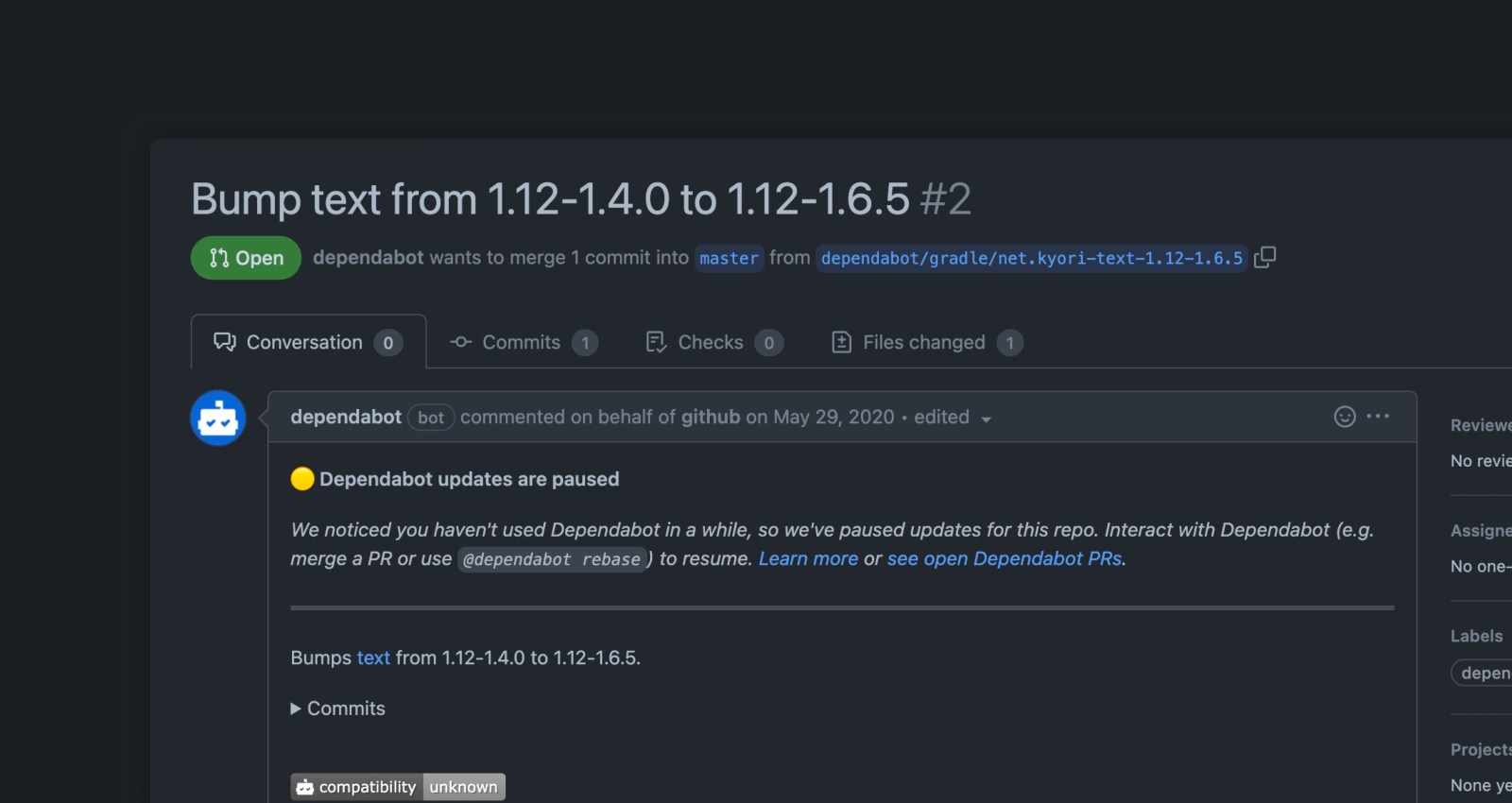
If Dependabot pull requests have been opened and rebased over time, but none of these pull requests have been merged, closed, or otherwise interacted with for 90 days, Dependabot will cease automated pull request activity and let you know.
What stays the same?
This change does not affect Dependabot alerts and their subsequent notifications. There’s also no change to manually requested Dependabot pull requests, which can still be generated from a Dependabot alert’s details page.
When will Dependabot activity be paused?
This change only applies to repositories where Dependabot pull requests exist but remain untouched. In other words, Dependabot will continue to automatically open and update pull requests until all the following criteria are true for at least 90 days:
- Has not had a Dependabot PR merged
- Has not had changes made to the Dependabot config file
- Has not had any @dependabot comment-ops performed
- Has not had any Dependabot PRs closed by the user
- Has received at least one Dependabot PR before the 90 day window
- Has at least one Dependabot PR open at the end of the 90 day window
- Has had Dependabot enabled for this entire period
Dependabot will also stop automatically rebasing pull requests after 30 days.
How will Dependabot let me know?
updated January 2024 to reflect the latest behavior
Dependabot will add a banner notice to open Dependabot pull requests, the repository settings page (under “Dependabot”) as well as your Dependabot alerts page (if Dependabot security updates are affected).

How do I wake Dependabot up?
Once you (so, not Dependabot) perform any of the following actions while Dependabot is paused, it will unpause itself:
- Merge a Dependabot pull request
- Close a Dependabot pull request
- Make a change to the Dependabot config file
- Manually trigger a security update
- Manually trigger a version update
- Enable security updates
- Use @dependabot commands on pull requests
Rollout begins today
This change will start to roll out today, expanding through January 2023 to include all repositories owned by individuals and by organizations with free and Team plans.
Shortly thereafter, it will roll out to GitHub Enterprise Cloud and GitHub Enterprise Server customers, where this improvement has the added benefit of enhanced efficiency with your self-hosted GitHub Actions runners.
Looking ahead
Moving forward, we will continue to work on making every Dependabot alert and pull request more relevant (with some larger undertakings currently underway, based on your feedback). Please continue to share your feedback on Dependabot–we’re listening!
Tags:
Written by
Related posts

How to catch GitHub Actions workflow injections before attackers do
Strengthen your repositories against actions workflow injections — one of the most common vulnerabilities.

Modeling CORS frameworks with CodeQL to find security vulnerabilities
Discover how to increase the coverage of your CodeQL CORS security by modeling developer headers and frameworks.

CVE-2025-53367: An exploitable out-of-bounds write in DjVuLibre
DjVuLibre has a vulnerability that could enable an attacker to gain code execution on a Linux Desktop system when the user tries to open a crafted document.