Cutting through the noise: How to prioritize Dependabot alerts
Learn how to effectively prioritize alerts using severity (CVSS), exploitation likelihood (EPSS), and repository properties, so you can focus on the most critical vulnerabilities first.

Dedicated to advancing the understanding and detection of software vulnerabilities—and explaining the latest vulnerability research from the GitHub Security Lab. Go behind the scenes with the GitHub Security Lab, a collaborative initiative that brings together security researchers, developers, and organizations to find and fix security vulnerabilities in open source software.

Learn how to effectively prioritize alerts using severity (CVSS), exploitation likelihood (EPSS), and repository properties, so you can focus on the most critical vulnerabilities first.


Learn how to identify which CVE Numbering Authority is responsible for the record, how to contact them, and what to include with your suggestion.
A step-by-step guide for open source maintainers on how to handle vulnerability reports confidently from the start.
Critical authentication bypass vulnerabilities (CVE-2025-25291 + CVE-2025-25292) were discovered in ruby-saml up to version 1.17.0. In this blog post, we’ll shed light on how these vulnerabilities that rely on a parser differential were uncovered.

Discover the exciting world of cybersecurity research: what researchers do, essential skills, and actionable steps to begin your journey toward protecting the digital world.
Learn how specially crafted artifacts can be used to attack Maven repository managers. This post describes PoC exploits that can lead to pre-auth remote code execution and poisoning of the local artifacts in Sonatype Nexus and JFrog Artifactory.

We are excited to introduce the new CodeQL Community Packs, a comprehensive set of queries and models designed to enhance your code analysis capabilities. These packs are tailored to augment…
In this post, I’ll walk you through the vulnerabilities I uncovered in the GStreamer library and how I built a custom fuzzing generator to target MP4 files.
Learn how I discovered 11 new vulnerabilities by writing CodeQL models for Gradio framework and how you can do it, too.
Learn about browser extension security and secure your extensions with the help of CodeQL.

As we wrap up Cybersecurity Awareness Month, the GitHub Bug Bounty team is excited to feature another spotlight on a talented security researcher who participates in the GitHub Security Bug Bounty Program—@adrianoapj!

For this year’s Cybersecurity Awareness Month, the GitHub Bug Bounty team is excited to feature another spotlight on a talented security researcher who participates in the GitHub Security Bug Bounty Program—@imrerad!

For this year’s Cybersecurity Awareness Month, GitHub’s Bug Bounty team is excited to offer some additional incentives to security researchers!
In this post, I’ll exploit CVE-2024-5830, a type confusion in Chrome that allows remote code execution (RCE) in the renderer sandbox of Chrome by a single visit to a malicious site.

In this blog post, we’ll explain how we discovered three critical vulnerabilities in Kafka UI and how they can be exploited.

In this post, I’ll exploit CVE-2024-3833, an object corruption bug in v8, the Javascript engine of Chrome, that allows remote code execution (RCE) in the renderer sandbox of Chrome by a single visit to a malicious site.

Can an attacker execute arbitrary commands on a remote server just by sending JSON? Yes, if the running code contains unsafe deserialization vulnerabilities. But how is that possible? In this blog post, we’ll describe how unsafe deserialization vulnerabilities work and how you can detect them in Ruby projects.

Let’s take a look at 10 key moments from the first decade of the GitHub Security Bug Bounty program.
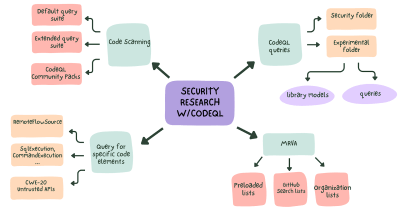
Learn how to use CodeQL for security research and improve your security research workflow.
Build what’s next on GitHub, the place for anyone from anywhere to build anything.